The Azure VPN Gateway supports a variety of connection methods for Point to Site VPN’s, one of the more interesting options that came out not too long ago is support for OpenVPN which is compelling as it ticks off a lot of boxes in terms of support such as:
- Tunnels over HTTPS so traverses firewalls easily
- Multi platform support - Windows, Mac OSX, iOS, Android, Linux
- RADIUS Authentication
- Can be used without Admin rights when setup correctly on Windows
The RADIUS authentication option is really interesting if you use Network Policy Server (NPS) included with Windows Server as you can hook in the Azure MFA Module to provide Multi factor Authentication. Unfortunately the Azure documentation does not outline the required NPS settings to support OpenVPN with RADIUS so after a support ticket, here is the required NPS configuration required to get this working:
Configure Azure
- Enable Point to Site VPN on your VPN Gateway and Select OpenVPN
- Pick an unused IP Range that is not part of a VNET’s range for your VPN Clients to use
- Set the IP of your RADIUS/NPS Server and the secret you will use
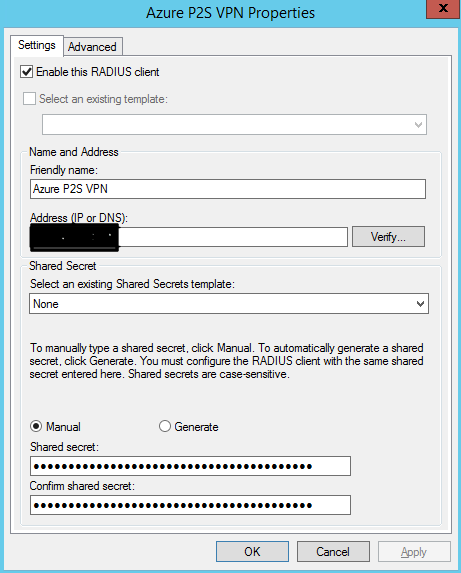
Configure RADIUS Client
In Network Policy Server, add a RADIUS client - the IP Address should be the subnet range of your GatewaySubnet
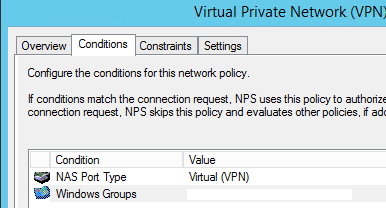
Configure Connection Request Policy
The key item in here is to Override the Authentication Methods, it must be configured as the picture below (Unencrypted PAP/SPAP)
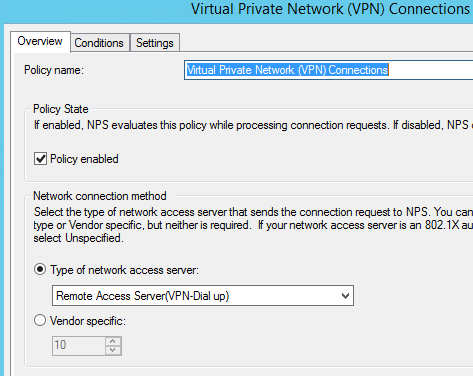
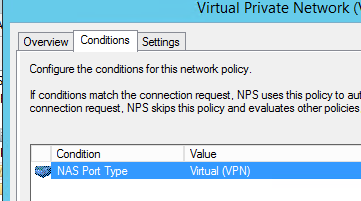
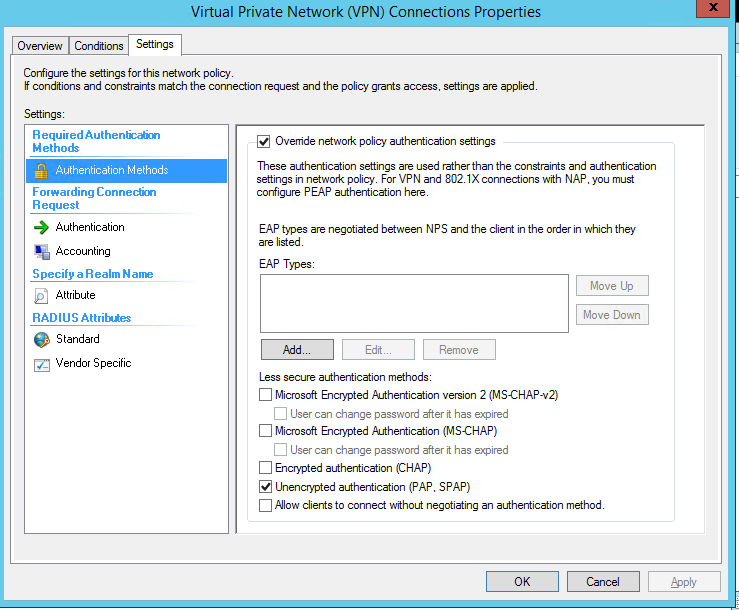
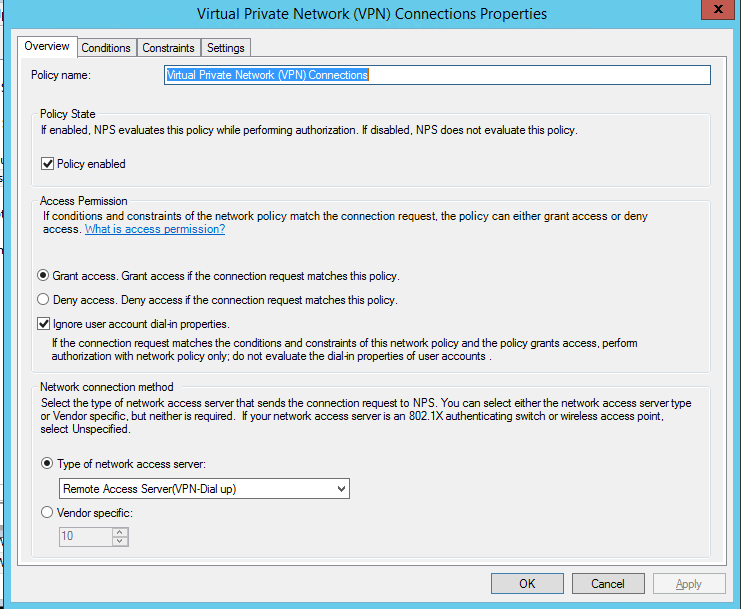
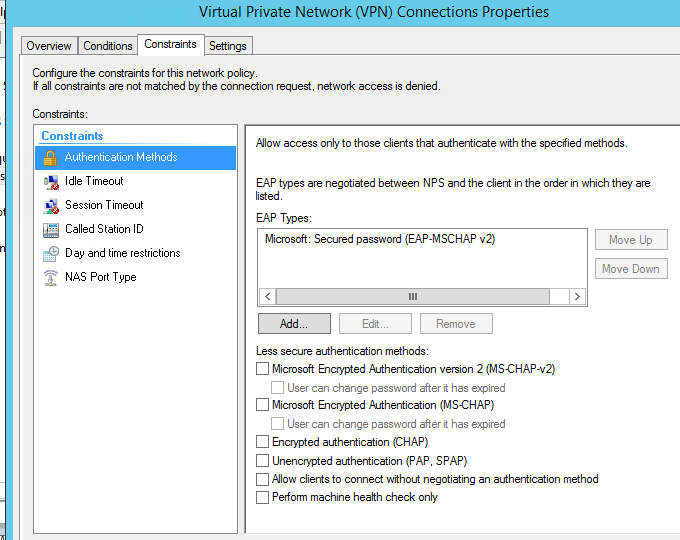
Configure Network Policy
Primary change is the constraints should be set to Microsoft: Secured Password (EAP-MSCHAP v2) if you are doing password based auth (which can then fire off to Azure MFA if setup)
Connect with OpenVPN
Download the VPN Configuration in the Azure Portal and load the OpenVPN connection profile - you should now be able to connect! I highly recommend setting up the Azure MFA module to secure the connection as well.